Is My Partners Information Again My Invite Link Is Expired
This browser is no longer supported.
Upgrade to Microsoft Border to have reward of the latest features, security updates, and technical support.
Azure Active Directory B2B collaboration invitation redemption
This article describes the means guest users tin access your resource and the consent process they'll encounter. If you send an invitation email to the invitee, the invitation includes a link the guest can redeem to get access to your app or portal. The invitation electronic mail is but one of the ways guests can get access to your resources. Every bit an culling, you lot can add guests to your directory and requite them a direct link to the portal or app you desire to share. Regardless of the method they use, guests are guided through a first-time consent process. This process ensures that your guests concur to privacy terms and accept any terms of employ you've set upwards.
When you add together a guest user to your directory, the invitee user account has a consent status (viewable in PowerShell) that's initially set to PendingAcceptance. This setting remains until the guest accepts your invitation and agrees to your privacy policy and terms of use. Afterwards that, the consent status changes to Accepted, and the consent pages are no longer presented to the guest.
Of import
- Starting July 12, 2021, if Azure AD B2B customers ready new Google integrations for employ with self-service sign-upward for their custom or line-of-business applications, authentication with Google identities won't work until authentications are moved to system web-views. Acquire more.
- Starting September xxx, 2021, Google is deprecating embedded spider web-view sign-in support. If your apps authenticate users with an embedded spider web-view and you're using Google federation with Azure Advertisement B2C or Azure Advertizement B2B for external user invitations or self-service sign-up, Google Gmail users won't be able to authenticate. Learn more.
- We've begun rolling out a change to turn on the electronic mail one-time passcode characteristic for all existing tenants and enable it by default for new tenants. Nosotros're enabling the email one-time passcode feature because information technology provides a seamless fallback authentication method for your guest users. Nonetheless, if you don't desire to allow this feature to turn on automatically, you can disable information technology. Soon, we'll stop creating new, unmanaged ("viral") Azure AD accounts and tenants during B2B collaboration invitation redemption.
Redemption and sign-in through a common endpoint
Guest users tin can now sign in to your multi-tenant or Microsoft first-political party apps through a common endpoint (URL), for instance https://myapps.microsoft.com. Previously, a common URL would redirect a guest user to their home tenant instead of your resource tenant for authentication, so a tenant-specific link was required (for case https://myapps.microsoft.com/?tenantid=<tenant id>). Now the guest user tin can go to the application's common URL, cull Sign-in options, and then select Sign in to an organisation. The user so types the name of your organization.
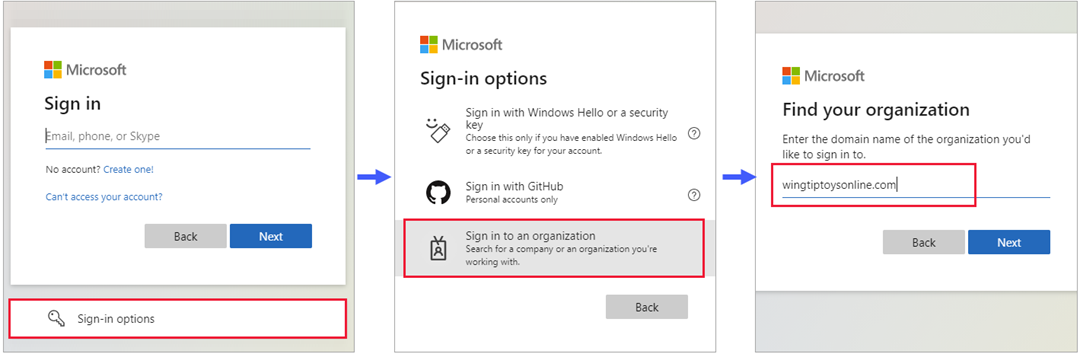
The user is then redirected to your tenanted endpoint, where they tin either sign in with their email address or select an identity provider you've configured.
Redemption through a straight link
As an culling to the invitation electronic mail or an application's common URL, you tin can give a invitee a straight link to your app or portal. You start need to add together the guest user to your directory via the Azure portal or PowerShell. So you tin can use whatsoever of the customizable ways to deploy applications to users, including straight sign-on links. When a guest uses a directly link instead of the invitation email, they'll nevertheless exist guided through the commencement-fourth dimension consent experience.
Note
A direct link is tenant-specific. In other words, it includes a tenant ID or verified domain and then the invitee tin can be authenticated in your tenant, where the shared app is located. Here are some examples of direct links with tenant context:
- Apps access panel:
https://myapps.microsoft.com/?tenantid=<tenant id> - Apps access panel for a verified domain:
https://myapps.microsoft.com/<;verified domain> - Azure portal:
https://portal.azure.com/<tenant id> - Individual app: see how to use a directly sign-on link
There are some cases where the invitation e-mail is recommended over a direct link. If these special cases are important to your organization, we recommend that you invite users by using methods that still send the invitation email:
- The user doesn't take an Azure AD account, an MSA, or an e-mail account in a federated organization. Unless you're using the one-fourth dimension passcode characteristic, the invitee needs to redeem the invitation email to be guided through the steps for creating an MSA.
- Sometimes the invited user object may not take an email address because of a conflict with a contact object (for example, an Outlook contact object). In this case, the user must click the redemption URL in the invitation e-mail.
- The user may sign in with an alias of the email address that was invited. (An alias is an boosted email accost associated with an email account.) In this case, the user must click the redemption URL in the invitation email.
Redemption through the invitation electronic mail
When you add a guest user to your directory by using the Azure portal, an invitation e-mail is sent to the guest in the process. You lot can as well cull to send invitation emails when you lot're using PowerShell to add together guest users to your directory. Hither's a clarification of the guest'south experience when they redeem the link in the e-mail.
- The guest receives an invitation email that's sent from Microsoft Invitations.
- The guest selects Accept invitation in the email.
- The guest will use their own credentials to sign in to your directory. If the guest does not accept an account that tin exist federated to your directory and the electronic mail ane-time passcode (OTP) feature is not enabled; the guest is prompted to create a personal MSA or an Azure AD self-service business relationship. Refer to the invitation redemption flow for details.
- The invitee is guided through the consent experience described below.
Sometimes the invited external guest user's email may conflict with an existing Contact object, resulting in the guest user being created without a proxyAddress. This is a known limitation that prevents invitee users from redeeming an invitation through a directly link using SAML/WS-Fed IdP, Microsoft Accounts, Google Federation, or Email Ane-Time Passcode accounts.
Withal, the following scenarios should continue to work:
- Redeeming an invitation through an invitation email redemption link using SAML/WS-Fed IdP, Email One-Time Passcode, and Google Federation accounts.
- Signing dorsum into an awarding later on redemption using SAML/WS-Fed IdP and Google Federation accounts.
To unblock users who can't redeem an invitation due to a alien Contact object, follow these steps:
- Delete the conflicting Contact object.
- Delete the invitee user in the Azure portal (the user'south "Invitation accepted" holding should exist in a pending country).
- Re-invite the guest user.
- Await for the user to redeem invitation.
- Add the user's Contact electronic mail back into Substitution and any DLs they should be a part of.
Invitation redemption flow
When a user clicks the Accept invitation link in an invitation email, Azure Advertising automatically redeems the invitation based on the redemption menses every bit shown below:
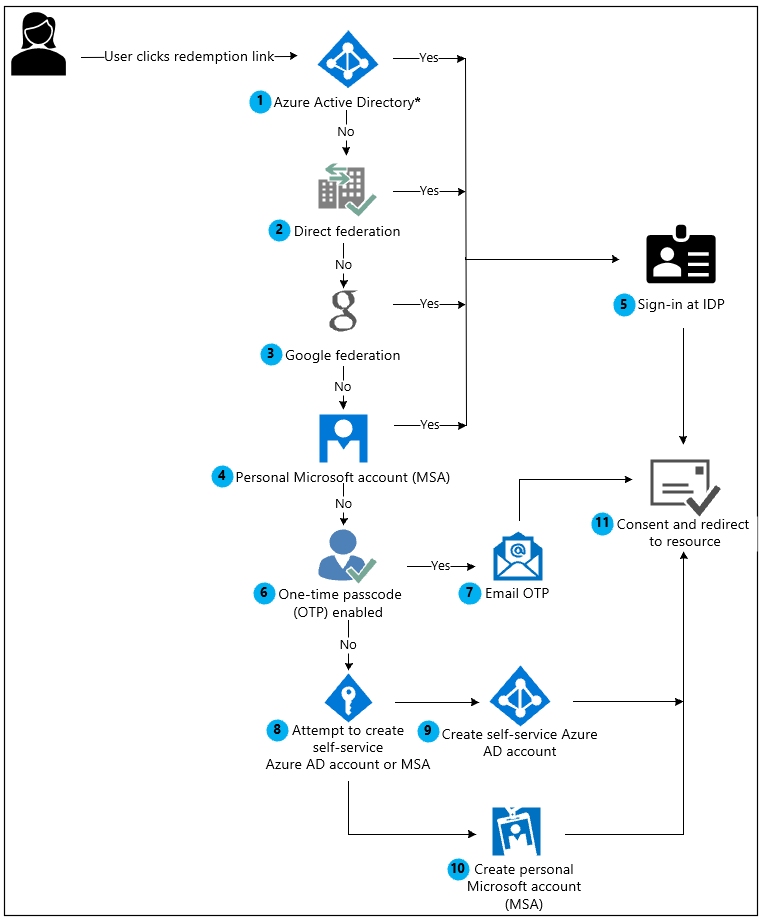
*If the user's User Master Proper noun (UPN) matches with both an existing Azure AD and personal MSA account, the user will be prompted to choose which account they want to redeem with.
-
Azure Advertizing performs user-based discovery to determine if the user exists in an existing Azure Advertisement tenant.
-
If an admin has enabled SAML/WS-Fed IdP federation, Azure Advertizing checks if the user'due south domain suffix matches the domain of a configured SAML/WS-Fed identity provider and redirects the user to the pre-configured identity provider.
-
If an admin has enabled Google federation, Azure AD checks if the user's domain suffix is gmail.com or googlemail.com and redirects the user to Google.
-
The redemption process checks if the user has an existing personal Microsoft account (MSA) for just-in-time (JIT) redemptions, but not for invitation email link redemption. If the user already has an existing MSA, they'll sign in with their existing MSA.
-
One time the user's home directory is identified, the user is sent to the corresponding identity provider to sign in.
-
If steps 1 to iv neglect to detect a dwelling house directory for the invited user, then Azure Advertizement determines whether the inviting tenant has enabled the email one-time passcode (OTP) characteristic for guests.
-
If e-mail one-time passcode for guests is enabled, a passcode is sent to the user through the invited email. The user volition remember and enter this passcode in the Azure Advertizement sign-in page.
-
If email quondam passcode for guests is disabled, Azure AD checks the domain suffix to make up one's mind if it belongs to a consumer business relationship. If so, the user is prompted to create a personal Microsoft account. If non, the user is prompted to create an Azure AD self-service account.
-
Azure Advertising attempts to create an Azure AD self-service account past verifying access to the email. Verifying the account is done by sending a code to the email, and having the user call back and submit it to Azure AD. However, if the invited user's tenant is federated or if the AllowEmailVerifiedUsers field is set to false in the invited user's tenant, the user is unable to consummate the redemption and the period results in an error. For more information, see Troubleshooting Azure Active Directory B2B collaboration.
-
The user is prompted to create a personal Microsoft business relationship (MSA).
-
Afterward authenticating to the right identity provider, the user is redirected to Azure AD to complete the consent experience.
For just-in-time (JIT) redemptions, where redemption is through a tenanted awarding link, steps eight through 10 are not bachelor. If a user reaches step half-dozen and the Email one-fourth dimension passcode feature is not enabled, the user receives an error message and is unable to redeem the invitation. To prevent this error, admins should either enable email quondam passcode or ensure the user clicks an invitation link.
Consent experience for the guest
When a guest signs in to a resource in a partner organization for the first time, they're presented with the following consent experience. These consent pages are shown to the guest only after sign-in, and they aren't displayed at all if the user has already accepted them.
-
The guest reviews the Review permissions page describing the inviting organisation's privacy statement. A user must Take the use of their information in accordance to the inviting organization's privacy policies to continue.

-
If terms of use are configured, the invitee opens and reviews the terms of use, and and then selects Take.
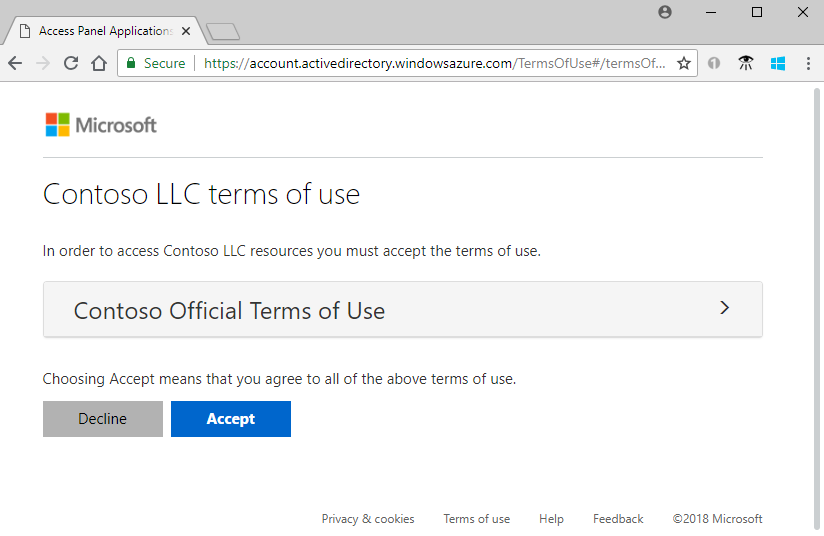
You can configure terms of use in External Identities > Terms of utilise.
-
Unless otherwise specified, the guest is redirected to the Apps access panel, which lists the applications the guest can admission.

In your directory, the guest's Invitation accustomed value changes to Yes. If an MSA was created, the guest'south Source shows Microsoft Account. For more than information near guest user account properties, see Properties of an Azure AD B2B collaboration user. If you run across an error that requires admin consent while accessing an application, see how to grant admin consent to apps.
Side by side steps
- What is Azure AD B2B collaboration?
- Add Azure Active Directory B2B collaboration users in the Azure portal
- How do information workers add B2B collaboration users to Azure Active Directory?
- Add Azure Agile Directory B2B collaboration users past using PowerShell
- Leave an organization equally a invitee user
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/active-directory/external-identities/redemption-experience
0 Response to "Is My Partners Information Again My Invite Link Is Expired"
Postar um comentário